

You are currently focusing on the certification. Go to program dashboard.
Your All Access Pass subscription has been suspended. Please contact us to resolve this issue.

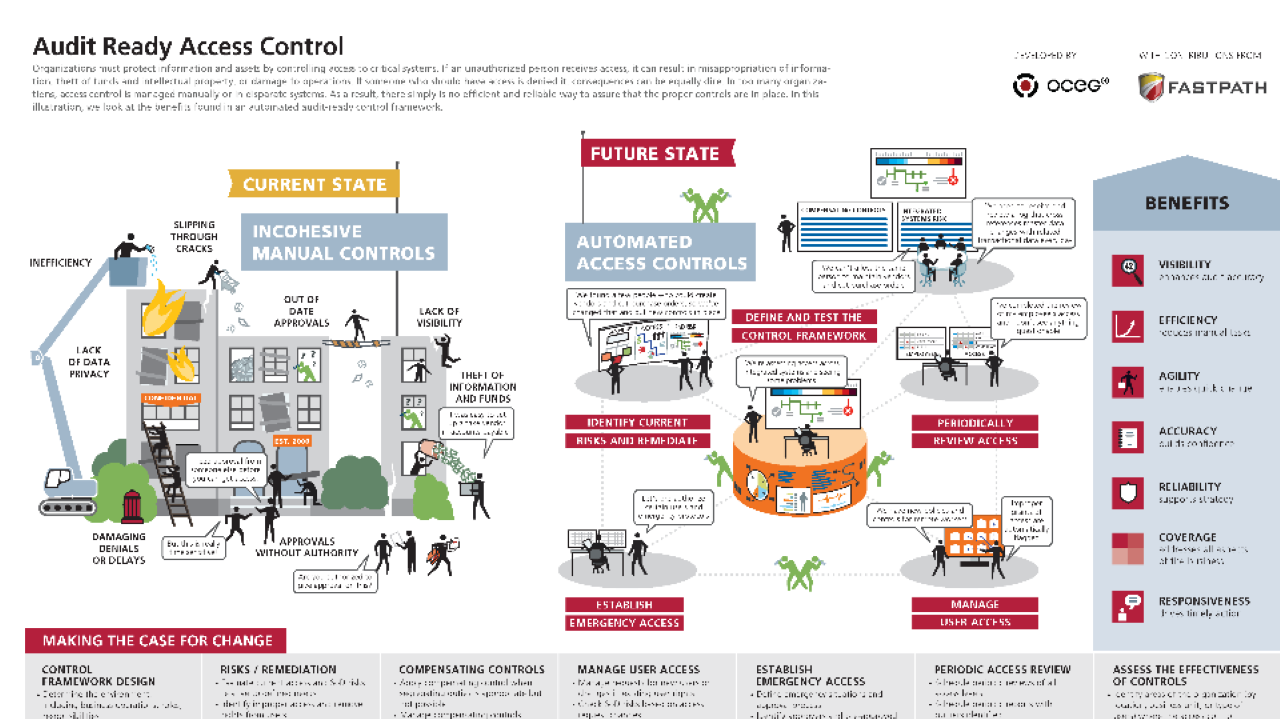
Organizations must protect information and assets by controlling access to critical systems.
Organizations must protect information and assets by controlling access to critical systems.
If an unauthorized person receives access, it can result in misappropriation of information, theft of funds and intellectual property, or damage to operations. If someone who should have access is denied it, consequences can be equally dire. In too many organizations, access control is managed manually or in disparate systems and there simply is no efficient and reliable way to provide assurance that the right controls are in place.
In this illustration, we look at the benefits found in an automated audit ready control framework.
Featured in: Controls , Assurance / Audit , Risk Management , Information Security
Like many websites, we use cookies and similar technologies such as session storage and analytics scripts to keep the site running smoothly and understand how visitors interact with our content. These tools may automatically collect technical information, including your device type, IP address, and browsing behavior.
By continuing to use this site, you acknowledge and accept this usage. For more information, please review our Terms of Service and Privacy Policy.
2942 N 24th St Ste 115 PMB 85352, Phoenix, AZ, 85016-7849, USA
Information & Billing
+1 (602) 234-9278
Principled Performance®, Driving Principled Performance®, Putting Principles Into Practice®, OCEG®, GRC360°®, ActiveLearning®, EventDay® and LeanGRC® are registered trademarks of OCEG®.
Protector Skillset™, Protector Mindset™, Protector Code™, Lines of Accountability™, GRC Professional™, GRCP™, GRC Fundamentals™, GRC Auditor™, GRCA™, GRC Audit Fundamentals™, Data Privacy Fundamentals™, Integrated Data Privacy Professional™, IDPP™, Policy Management Fundamentals™, Integrated Policy Management Professional™, IPMP™, Integrated Audit & Assurance Professional™, IAAP™, Integrated Governance & Oversight Professional™, IGOP™, Integrated Strategy & Performance Professional™, ISPP™, Integrated Risk Management Professional™, IRMP™, Integrated Decision Management Professional™, IDMP™, Integrated Compliance & Ethics Professional™, ICEP™, Integrated Business Continuity Professional™, IBCP™, Integrated Information Security Professional™, IISP™ are trademarks of OCEG®.

